Frequently Asked Questions
General
Which browsers support AffirmTrust certificates?
What is the difference between DV, OV, and EV certificates?
Do I need to install the AffirmTrust root certificate?
How do you know that you are accessing a trusted server?
How do I get 128-bit or 256-bit secure web sessions?
Should I use SHA-1 or SHA-2 for my certificates?
What is a wildcard certificate?
How long are AffirmTrust certificates valid?
Certificate Signing Request (CSR)
How do I create a Certificate Signing Request (CSR)?
Can I use a CSR with a 1024-bit key length?
What should I do if I get a "CSR cannot be decoded or is invalid" message?
What is a weak RSA key?
Setup
Installing SSL Certificates
Where can I find and download the intermediate certificates I need?
Which web servers are compatible with AffirmTrust certificates?
Do I need to install the AffirmTrust root certificate?
Do I require the AffirmTrust chain certificate?
How many AffirmTrust certificates are required in a load-balancing environment?
How many servers can I secure with one SSL certificate?
Can I secure my top-level domain with and without the "www." sub-domain?
How do I renew an AffirmTrust certificate with IIS?
What is Subject Alternative Name (SAN)?
I have moved servers. Can I use the same AffirmTrust certificate?
Troubleshooting SSL Issues in AffirmTrust
Losing the private key for the SSL certificate
Changing the common name after the certificate has been issued
Testing whether the SSL certificate is installed correctly
The page loads over https without error, however, the padlock does not appear
Receiving a warning stating that the page contains both secure and non-secure items
The name of the security certificate is invalid or does not match the name of the site" message appears
Extended Validation (EV) Certificates
What is an EV SSL certificate?
Are non-EV SSL certificates still sufficient for securing online transactions?
How do AffirmTrust EV certificates increase consumer confidence?
Should I switch to AffirmTrust EV certificates?
What is the CA/Browser Forum?
What is the EV certificate vetting process?
Does the AffirmTrust EV certificate show the green address bar?
How do browsers respond when they visit a website with an invalid certificate?
Can I get free reissues of my EV certificates?
Who can purchase a AffirmTrust EV certificate?
What are the validation requirements for Extended Validation (EV) SSL certificates?
General
Which browsers support AffirmTrust certificates?
The AffirmTrust SSL root certificate is embedded in most major browsers. This means that SSL certificates issued by AffirmTrust SSL are trusted automatically and transparently by greater than 99% of browsers, providing maximum end-user security and usability.
What is the difference between DV, OV, and EV certificates?
Domain Validated (DV) SSL
Where the CA only checks the right of the applicant to use a specific domain name via an email challenge. No company information is checked and therefore company information is not displayed within the certificate. Although this means that issuance time is fast (often in minutes), this is a very low value certificate and is the topic of much debate in the industry—some members of the CA/Browser Forum believe that this type of SSL certificate should not be allowed due to the fact it delivers a false sense of security.
Organization Validated (OV) SSL
Provides a basic level of vetting of an organization before issuance of a trusted SSL certificate. Issuing CAs check the right of the applicant to use the specified domain name and also check into the existence of the organization itself. This vetted company information is displayed to customers when viewing the certificate details, giving more visibility into the organization behind the site. Much more secure than a DV certificate, issuance of an OV certificate can often take days due to the requirement to vet the organization.
Extended Validation (EV) SSL
Delivers the highest level of consumer trust through the strictest authentication standards of any SSL certificate. Extended Validation verification guidelines, created by an independent body, require issuing CAs to obtain and verify multiple pieces of identifying information about the Organization and Organizational Contact listed in the enrollment. EV Certificates enable consumers to easily understand that they are on the correct website through visual cues, including the very obvious green bar that shows up in the browser. For Extended Validation vetting guidelines, refer to the following CA/Browser Forum topic: Overview of the Extended Validation SSL Certificate Vetting Process.
Do I need to install the AffirmTrust root certificate in my browser?
Once you properly install the certificate chain on your web server, AffirmTrust will be trusted across more than 99% of browsers being used today. Most users will have the AffirmTrust root certificate installed. However, if you do not have it installed and you visit a site secured with an AffirmTrust certificate, the browser will ask you whether you want to trust certificates issued by AffirmTrust. If they answer yes, the AffirmTrust root certificates will be installed automatically. If they answer no, you can still opt to work within the secure session, but will be prompted again the next time you visit the site.
How do you know that you are accessing a trusted server?
When you access a server secured with an AffirmTrust certificate, you will see a padlock at the bottom, top, or in the address bar of your browser. If you click the padlock, you will see the details of the server’s SSL certificate. If the server is secured with an AffirmTrust EV certificate, the browser address bar turns green in all browsers that support the EV standard, including Internet Explorer, Firefox, Opera, Chrome, and Safari.
How do I get 128-bit or 256-bit secure web sessions?
The strength of the Secure Sockets Layer (SSL) session created using AffirmTrust certificates is related to the strength of the user’s browser and your web server policy. If the browser supports 128-bit encryption, then a 128-bit session will be established with the web server. The same is true for 256-bit encryption.
If the browser only supports 40-bit encryption, then only a 40-bit session will be established – even if your web server supports 128 or 256-bit sessions. If the browser only supports 40-bit encryption, AffirmTrust recommends upgrading to the latest supported version of the browser.
Should I use SHA-1 or SHA-2 for my certificates?
You may only order a SHA-2 certificate. SHA-2 is a newer and stronger cryptographic algorithm than SHA-1. SHA-2 certificates are supported on most modern browsers, operating systems, mail clients, and mobile devices.
What is a wildcard certificate?
A wildcard SSL certificate enables you to secure a website’s domain and an unlimited number of its subdomains. For example, a single wildcard certificate could secure both www.example.com, anddeals.example.com.
Wildcard certificates enable the securing all of the subdomains at the level specified when you submit your certificate request. Add an asterisk (*) in the subdomain part of the common name (CN) where you want to use the wildcard.
Examples:
If you configure *.example.com, you can secure www.example.com, deals.example.com, info.example.com, etc.
If you configure *.www.example.com, you can secure mail.www.example.com, deals.www.example.com, info.www.example.com, etc.
Note: A wildcard certificate secures only the level of subdomain you specify. So, if a certificate is configured for*.www.example.com, it will not secure www.example.com.
Wildcard certificates secure websites the same way as a regular SSL certificate, and requests are processed using the same validation methods. However, some web servers may require a unique IP address for each subdomain on the wildcard certificate.
Note: Extended Validation (EV) certificates do not support the concept of a wildcard, but they do work with Subject Alternative Names (SANs), which enable the use of extra fully-qualified domain names and subdomain names.
How long are AffirmTrust certificates valid?
With your AffirmTrust account, you can issue OV and EV SSL certificates with either a 1 year or 2 year validity period.
Certificate Signing Request (CSR)
How do I create a Certificate Signing Request (CSR)?
Creating a Certificate Signing Request (CSR)
Before you send a request for an SSL certificate, you must create a Certificate Signing Request (CSR) on the server that you want to secure.
DETAILS
A CSR is an encrypted file that contains information about your company, including the domain name.
The CSR must include this information:
- Country: Two-letter ISO 3166 country code. For example, the code for the Japan is "JP". For other countries, see the ISO list of country codesor here.
- State or Province: Full name of the state or province where your company is headquartered, such as "California".
- Locality or City: Full name of the locality or city where your company is headquartered, such as "Los Angeles".
- Organization: Full legal name of your company.
- Common Name:The website that you will protect with the SSL certificate.
Note: If a certificate request contains an IP address (such as 198.30.21.143), the certificate cannot be issued. The certificate request may contain a fully qualified domain name (www.example.com), second-level domain (example.com), or a wildcard domain (*.example.com). All domain names must be publicly registered. Domains not publicly registered are considered internal server names (ISNs). Due to CA/Browser Forum requirements, the support for certificates that contain an ISN has been deprecated. Certificates containing an ISN are restricted to the OV level and must expire before November 1, 2015. In addition, certificates containing an ISN must be manually vetted, which may delay their issuance.
Note: Do not use blank fields in your CSR. If you do not wish a field to be in your certificate, simply do not include this field in your CSR. AffirmTrust does not currently support the use of "Organizational Unit" fields in CSRs. If you include an Organizational Unit field, it will be ignored.
The process used to create a CSR depends on the server that you are securing.
For Microsoft servers, download the following documentation: Creating a CSR for Microsoft.
For Apache servers, download the following documentation: Creating a CSR for Apache.
For other servers, download the following documentation: Creating a CSR for other servers.
- C2Net Stronghold
- Cisco Adaptive Security Appliance (ASA) 5500
- Cobalt RaQ4/XTR
- F5 BIG IP (version 9)
- F5 BIG IP (pre-version 9)
- F5 FirePass VPS
- HSphere Web Server
- IBM HTTP Server
- Java-based web server (generic)
- Lotus Domino 8.5
- Mirapoint
- Nginx
- Oracle Wallet Manager
- Oracle WebLogic Server 8 or 9
- Plesk 10
- Plesk 9
- Plesk 8
- SAP Web Application Server 6.10 or higher
- Zeus Web ServerPremium
Can I use a CSR with a 1024-bit key length?
No. Recommendations from the National Institute of Standards and Technology (NIST) and mandatory requirements of the Microsoft Root Certificate Program state that certificates issued after January 1, 2011 should have a minimum key length of 2048 bits. To fully comply with these recommendations, all AffirmTrust certificates require a minimum key length of 2048 bits.
What should I do if I get a "CSR cannot be decoded or is invalid" message?
The CSR can contain any of the following fields, but those marked mandatory must be included in order for the CSR to be processed successfully. Take note that Microsoft Windows IIS will not allow you to include the email address in your CSR.
- Organization (Mandatory)
- Locality (City) (Mandatory)
- State/Province (Mandatory)
- Country (2 character code) (Mandatory)
- Common Name (Mandatory)
- Email Address
Another possibility is that the CSR contains illegal characters in one of the fields. The fields can only contain alpha-numeric characters, with the exception of the Common Name and Email Address fields, which can also include the ‘@' and ‘.’ characters.
Note: Ensure that your CSR begins and ends with 5 dashes, as shown below:
-----BEGIN NEW CERTIFICATE REQUEST-----
-----END NEW CERTIFICATE REQUEST-----
If you are renewing your SSL certificate, you must create a new CSR; you cannot simply use the previous CSR because a new pending request and private key must be generated on your web server for the process to work.
If you are renewing using IIS, you cannot use the ‘renew certificate’ option on IIS, but must instead create a new CSR.
What is a weak RSA key?
Between 2006 and 2008, the Debian OpenSSL library contained a bug that resulted in the generation of weak, predictable keys for SSL certificates and other uses. The bug also compromises other keys and passwords that are transmitted over an encrypted link that uses weak keys.
When you request an SSL certificate by pasting a CSR into the AffirmTrust console, the console checks whether the CSR contains a Debian weak key. If the CSR contains a weak key, you will need to upgrade to the new version of the OpenSSL package and create a new CSR.
Setup
Installing SSL Certificates
After you submit the CSR and receive your SSL server and intermediate certificates, you need to install them on your server.
Your AffirmTrust end-entity certificate must be installed with other intermediate certificates in the trust chain in order to be trusted (display the padlock or green bar) in the major browsers and applications. AffirmTrust certificates are issued off the AffirmTrust Commercial root. The root and intermediate CA certificates you need to install on your servers may include the following certificates, depending on which type of certificate you use:
- AffirmTrust Extended Validation CA – EV1
- AffirmTrust Certificate Authority – OV1
For Microsoft servers, download the following documentation: Installing certificates for Microsoft.
For Apache servers, download the following documentation: Installing certificates for Apache.
For other servers, download the following documentation: Installing certificates for other servers.
This documentation includes instructions on how to install certificates on the following servers:
- C2Net Stronghold
- Cisco Adaptive Security Appliance (ASA) 5500
- Cobalt RaQ4/XTR
- F5 BIG IP (version 9)
- F5 BIG IP (pre-version 9)
- F5 FirePass VPS
- HSphere Web Server
- IBM HTTP Server
- Java-based web server (generic)
- Lotus Domino 8.5
- Mirapoint
- Nginx
- Oracle Wallet Manager
- Oracle WebLogic Server 8 or 9
- Plesk 10
- Plesk 9
- Plesk 8
- SAP Web Application Server 6.10 or higher
- Zeus Web Server Premium
Where can I find and download the intermediate certificates I need?
The intermediate certificates you need are available at two places.
You can find and download the intermediate certificates on the same page in the Customer Portal where you downloaded your server certificate:
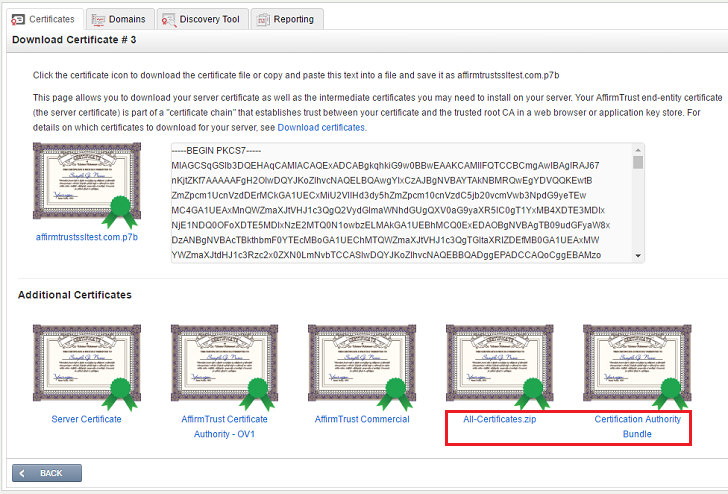
At the bottom of the screen are download links for the intermediate certificates you need, including two bundles:
ALL-CERTIFICATES.ZIP and
CERTIFICATE AUTHORITY BUNDLE.
The ALL-CERTIFICATES.ZIP file includes the following certificates (your server certificate and two CA certificates):
- Affirmtrust_Commercial.crt
- One of AffirmTrust Certificate Authority – OV1.crt
or
AffirmTrust Extended Validation CA – EV1.crt - your.server.name.crt
The CERTIFICATE AUTHORITY BUNDLE contains two CA certificates in a single .crt file. It is designed to be used for Apache openssl servers. You can download this file and use it directly in the Apache openssl server configuration line SSLCertificateChainFile:
- Affirmtrust_Commercial.crt
- One of AffirmTrust Certificate Authority – OV1.crt
or
AffirmTrust Extended Validation CA – EV1.crt
Note: Make a backup copy of your SSL certificates and keep them in another location.
Which web servers are compatible with AffirmTrust certificates?
AffirmTrust certificates can be issued for any server that is compatible with the x.509 v3 standard and is able to make a certificate request in PKCS#10 format. This includes most recent servers, including:
- Microsoft Internet Information Server (IIS) v3 or higher
- Microsoft Communications Server
- Apache
- Nginx
- Netscape Enterprise Server v3 or higher
- Netscape Commerce Server v1 or higher
- Netscape FastTrack Server
- Stronghold Server
- Internet Application Server 1.0
- Netscape iPlanet Web Server 4.1
For Apache and Nginx Servers, Open SSL is needed.
Do I need to install the AffirmTrust root certificate in my server?
Normally, when you install an SSL certificate, you also need to install the intermediate CA certificates but not the root certificate. Unless your server vendor specifically requires you to install the root certificate, you should not install it on your web server.
You can download all of the required certificates from the AffirmTrust console. Click the Common Name of the certificate. On the Details page, click Download.
Do I require the AffirmTrust chain certificate?
Yes.
How many AffirmTrust certificates are required in a load-balancing environment?
You need one AffirmTrust certificate for each of your secure web servers (including any virtual web servers). With a certificate account, there are no additional costs to support this.
How many servers can I secure with one SSL certificate?
AffirmTrust certificates are provided with licensing for an unlimited number of servers included in the standard price. This allows you to easily secure your primary server, a secondary or backup server, and a load balancer.
To move your certificate between servers, you need to install the certificate on the web server where you generated the CSR and then export the SSL certificate and its private key to a PFX or PKCS12 file. You can then import that file on another web server.
Can I secure my top-level domain with and without the "www." sub-domain?
Yes. With AffirmTrust certificates, if you purchase an SSL certificate to secure www.example.com, it will also secure example.com.
How do I renew an AffirmTrust certificate with IIS?
IIS 7
- Create a new CSR.
- Complete the pending request.
- Go to your "Default Web Site" and right-click on EDIT Bindings. Click ADD and select the new certificate from the drop-down list.
IIS 5 or IIS 6
This process allows you to renew your expiring SSL certificate on IIS without experiencing any downtime on your website. By following these steps, you will be able to maximize your uptime and the overall security of your site:
- On your Windows server, open the Internet Information Services (IIS) Manager. Click Start > Programs > Administrative Tools > Internet Information Services Manager.
- Create a temporary site in IIS. Right-click on the main server node (local computer) and click New > Web Site. You can call it anything you want (for example, temporarysite). You will delete the temporary site later so the setup details are not important.
- Generate a Certificate Signing Request (CSR) for the dummy site. The Common Name (Example: www.example.com) in the new CSR must be the same as your real site. For example, if the certificate you’re trying to renew is for secure.example.com then the Common Name in the CSR for the dummy site will also need to be secure.example.com. To generate the CSR, refer to the article: Creating a Certificate Signing Request.
- In the AffirmTrust SSL Portal, use the CSR that you created to reissue the certificate.
- AffirmTrust will issue your SSL certificate and return it to you by email. Copy the certificate into a text editor such as Notepad and save as yourdomain.cer on your desktop.
- Return to the Directory Securitytab of your temporary site and select Server Certificate. Then select Process the pending request and install the certificate and click Next.
- Locate the yourdomain.cer file when prompted to locate your web server certificate and click Next.
- On the summary screen, check the expiration data to ensure that you are processing the correct certificate and click Next.
- On the confirmation screen, click Nextand then Finish. The SSL certificate is now installed on the temporary site. Next, you will transfer it to the real site.
- Right-click your real website and click Properties.
- On the Directory Security, under Secure communications, click Server Certificate.
- In the Welcome to the Web Server Certificate Wizard window, click Next.
- Select Replace the current certificateand click Next.
- You will be asked to select your SSL certificate from a list of installed certificates. Ensure you select the new certificate from the list.
- On the summary screen, check the expiration data to ensure that you are processing the correct certificate. Click Next.
- On the confirmation screen, click Nextand then Finish. Your old SSL certificate has now been replaced with the new certificate from the temporary site. You may safely delete the entire temporary site.
What is Subject Alternative Name (SAN)?
Subject Alternative Names (SANs) enable you to secure multiple host names with one SSL certificate.
The SAN extension has been included in the X509 certificate standard for more than 10 years, but became widely used after the launch of Microsoft Exchange Server 2007, which uses SANs to simplify server configuration.
There are several situations where you may want to add SANs to your certificate:
- You can use one SSL certificate to secure host names on different base domains. A wildcard certificate like *.example.com can protect all first-level subdomains on one domain, but a wildcard cannot protect both www.example.com and example.net.
- Hosting multiple SSL-enabled sites on a single server typically requires a separate IP address for each site, but a certificate with SANs can solve this problem. Microsoft IIS 6 and Apache are both able to Virtual Host HTTPS sites using Unified Communications SSL, also known as SAN certificates.
- SAN certificates simplify your Exchange Server 2007 SSL configuration. If you use a SAN certificate, you do not need to configure multiple IP addresses on your Exchange 2007 server.
I have moved servers. Can I use the same AffirmTrust certificate?
Providing that the domain name does not change, you can use the same. Export the SSL certificate from the old web server and import it into the new one. Both the certificate and its associated private key must be exported and then imported, and the method for completing the export/import will depend on the type of web server software you are using.
Troubleshooting SSL Issues in AffirmTrust
Losing the private key for the SSL certificate
AffirmTrust SSL certificates can be reissued as many times as needed for the entire validity period of your portal.
If you lose your private key, you can either:
- Issue a brand new certificate, or
- Generate a new Certificate Signing Request (CSR), log in to the AffirmTrust SSL portal, go to the My Certificates tab, click the order number of the certificate, and click Reissue. Paste your CSR into the text box on the page and click Continue.
Changing the common name after the certificate has been issued
The name of the site is specified in the "Issued to" field of the certificate. This name must match whatever is being displayed in the address bar. The "common name" of the certificate cannot be changed without invalidating the certificate. The only course of action would be to generate a new Certificate Signing Request (CSR), this time specifying the correct common name, and then to order a new certificate.
"Page Cannot Be Displayed" error
Possible causes and solutions:
- Firewall or router is blocking the secure port (typically port 443): Ensure that port 443 is open and allows traffic through.
- Port 443 has been assigned for SSL by the web server: In Microsoft IIS, you will need to enter 443 into the SSL port on the website tab of your site. In Apache, you will need to specify ":443" in the virtual host section pertaining to your website.
- Private Key Modulus does not match the Public Key Modulus: If you submit the key file and the certificate file to support, we can check to determine whether the moduli match. If they do not match then it is likely that there has been a mix up with their private keys or the private key has been deleted. If the private key cannot be found you will need to start again and create a new private key and CSR and have the certificate reissued.
- The web server is not configured properly: There must be a unique IP address assigned to the website. In IIS, the IP address detailed in the IP address field on the website tab of your site must be specified in the Advanced section (click Advanced next to the SSL Port entry). If All Unassigned is present, remove it and add the IP address. You cannot use Host Headers in IIS. Unix-based web servers (Apache, control panels such as Plesk, Ensim) must be in IP-based mode and not in name-based mode. A unique IP address must be specified in the virtual host section of the site.
- Ensure there is only 1 IP per certificate: Otherwise, conflicts will occur.
- DNS Issues: A site will either have an internal or external IP address. Find out which one you are using. The IP address must route to the domain name somehow.
- Can the site be accessed via the IP address? If the domain name has been recently purchased, then the DNS records needs to propagate (24-72 hours). If an internal IP address is being used, then a Network Address Translator (NAT), Firewall, or router must route the internal IP address to an external IP address in order for the site to be found externally.
- Some web servers require a physical reboot. Leave this option to last as it can cause disruption to service levels of the hosting company
Testing whether the SSL certificate is installed correctly
To test your new certificate, open a browser and type your server’s Fully Qualified Domain Name with https://, for example:
https://www.example.com
Always ensure that Port 443 is open on your firewall.
The page loads over https without error, however, the padlock does not appear
This is probably because the SSL link is being severed by a BASE command in the < head > section of the page. View the HTML and check whether there is a line like this in the < head > section at the top of the page:
< BASE href="http://www.example.com" >
This line forces all relative links to revert to http. Because of this, the SSL session cannot be established and the padlock cannot appear. You will need to remove the < BASE href="http://www.example.com " > code from the page and make sure that there are no further file references using http:// on the page.
Alternatively, you can change the line in the < head > section at the top of the page to read as follows:
< BASE href="https://www.example.com " >
This will set all relative links to https mode and allow the padlock to appear
Receiving a warning stating that the page contains both secure and non-secure items
This can occur if you are forcing the web server to load content over http rather than https when you are in SSL mode. Check your HTML code and ensure that you have no references to files or graphics that start with src=http://www. example.com/directory/file.gif.
If you do have reference like this, they must be relative, such as src=/directory/file.gif or absolute using https, such as src=https://www.example.com/directory/file.gif.
The name of the security certificate is invalid or does not match the name of the site" message appears
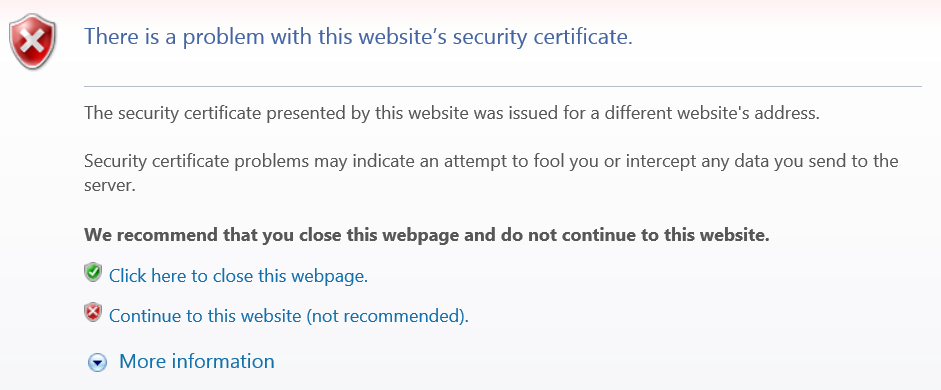
This error occurs when the certificate is being used on a different fully qualified domain name (FQDN) than the one for which it was issued. For example, if your certificate was issued to www. example.com, using it on secure. example.com will result in a name mismatch error.
You may also see this Security Alert if you have not installed the intermediate certificate and rebooted your server.
Extended Validation (EV) Certificates
What is an EV SSL certificate?
Delivers the highest level of consumer trust through the strictest authentication standards of any SSL certificate. Extended Validation verification guidelines, created by an independent body, require issuing CAs to obtain and verify multiple pieces of identifying information about the Organization and Organizational Contact listed in the enrollment. EV Certificates enable consumers to easily understand that they are on the correct web site through visual cues, including the very obvious green bar that shows up in the browser. For Extended Validation vetting guidelines, refer to the following CA/Browser Forum topic: Overview of the Extended Validation SSL Certificate Vetting Process.
Are non-EV SSL certificates still sufficient for securing online transactions?
From a cryptographic security perspective, yes, non-EV SSL certificates still result in encrypted SSL sessions. However, the greatest threat to online transactions is not cryptographic in nature – it is fraudulent web sites luring users with phishing attacks. Phishing uses social engineering and counts on a consumer’s inability to discern between trustworthy sites and imposter sites.
The EV initiative is the result of the industry realizing that there needs to be a more readily-identifiable for users to know they are on a valid site. From a usability perspective, non-EV certificates have decreasing effectiveness, as consumers adopt new browsers and come to expect the strong trust indicators provided by EV SSL certificates while conducting transactions.
How do AffirmTrust EV certificates increase consumer confidence?
With online fraud on the rise and phishing becoming a common occurrence, consumers are concerned with identity theft and would like increased confidence in the sites they use to perform transactions online. If consumers feel the site is not trusted and their personal information is unprotected, they may leave the site and take their business to another vendor.
AffirmTrust EV certificates help to increase consumer confidence by displaying prominent and consistent trust indicators while consumers are conducting online transactions. When a website has a AffirmTrust EV certificate installed:
- A lock appears in the address bar of the browser
- The address bar turns green and displays the identity of the site.
- You can click the lock to view information about the server’s SSL certificate.
Should I switch to AffirmTrust EV certificates?
If you are operating a website that conducts e-commerce transactions or if you collect sensitive or private information, you should consider switching to AffirmTrust EV certificates.
What is the CA/Browser Forum?
The CA/Browser Forum is a group of Certification Authority service providers, web browser manufacturers, and other industry participants that work together to look at ways to reduce the threat of phishing and other internet attacks.
AffirmTrust actively works in this group and strongly supports its work.
What is the EV certificate vetting process?
As defined by the CA Browser (CAB) Forum guidelines, the Extended Validation vetting process establishes the legitimacy of an organization within a specific jurisdiction of incorporation. It also clearly identifies the organization’s principal place of business through a rigorous and stringent set of well-defined validation processes. The process encompasses authentication of the organization’s domain ownership rights as well as contractually binding the organization to a subscriber agreement, which benefits relying parties and strengthens the security of the Internet as a whole.
Does the AffirmTrust EV certificate show the green address bar?
The use of an EV certificate will turn the browser address bar green in all browsers that support the EV standard, including Internet Explorer, Firefox, Opera, Chrome, and Safari.
Internet Explorer 7 requires that the phishing filter be turned on in order for the address bar to turn green.
How do browsers respond when they visit a website with an invalid certificate?
In most browsers, a very apparent red address bar will appear, indicating that you may have accessed a known phishing site or that the certificate is not valid in some way. A red alert blocks immediate access to reported phishing sites, although users can proceed to the site if they wish.
Internet Explorer includes prominent warnings to users and will recommend users not visit the page. If the user ignores the warnings and continues the address bar turns red and red warning ‘security badges’ appear.
Can I get free reissues of my EV certificates?
Absolutely. This can all be done easily through the AffirmTrust console.
Who can purchase a AffirmTrust EV certificate?
A broad range of business entities, as per rigid guidelines, are able to purchase an EV certificate:
Private Organization: A non-governmental legal entity (whether ownership interests are privately held or publicly traded) whose existence was created by a filing with (or an act of) the Incorporating Agency in its Jurisdiction of Incorporation.
Government Entity: A government-operated legal entity, agency, department, ministry, or similar element of the government of a country, or political subdivision within such country (such as a state, province, city, county, etc.).
Business Entity: Any entity that is neither a Private Organization nor a government entity. Examples include general partnerships, unincorporated associations, and sole proprietorships.
Can I upgrade my existing SSL certificates to an AffirmTrust EV certificates?
Yes. With some additional effort (as mandated under the EV guidelines), your organization can deploy EV certificates to your online businesses and enjoy the increased confidence they bring to end users.
What are the validation requirements for Extended Validation (EV) SSL certificates?
Organization Authentication Requirements
The following entities are eligible to receive an EV certificate provided they are currently registered with and approved by an official registration agency in their jurisdiction. The resulting charter, certificate, license or equivalent must be verifiable through that registration agency.
- Government agencies
- Corporations
- General partnerships
- Unincorporated associations
- Sole proprietorships
AffirmTrust must be able to confirm all of the following organizational registration requirements:
Official government agency records must include:
- The organization’s registration number
- The organization’s date of registration/incorporation
- The organization’s registered address
A non-government data source (such as Dun & Bradstreet) must include the organization’s place of business address if it is not included in the Government agency records.
If the organization has been registered for less than three years, AffirmTrust must verify operational existence through one of the following means:
- Through a non-government data source (such as Dun & Bradstreet) or
- By verifying the organization has an active demand deposit account (such as a checking account) with a regulated financial institution through a Professional Opinion Letter or directly with the financial institution.
Domain Authentication Requirements
To qualify for an Extended Validation SSL certificate, domain registration details must reflect the full organization name as included in the certificate request. Where domain registration does not reflect the organization name as identified in the certificate request, positive confirmation of the organization’s exclusive right to use the domain name is required from the registered domain administrator or with a professional opinion letter.
- The domain must be registered with ICANN or IANA registrar (for CCTLDs). Domain registration details must be updated to reflect the organization name as included on the certificate request.
- Where domain registration is private, the domain registrar is required to unblock the privacy feature.
- The organization’s organizational contact must confirm knowledge of the organization’s domain ownership during the verification call.
Organization’s Organizational Contact Authentication Requirements
To qualify for an Extended Validation SSL certificate, the organizational contact identified in the certificate request must be employed by the requesting organization and have appropriate authority to obtain and delegate EV certificate responsibilities.
- Employment and authorization cannot be verified through the organization’s web site.
- If the organizational contact identified in the certificate request is listed in government records as a corporate officer (such as Secretary, President, CEO, CFO, COO, CIO, CSO, Director, or equivalent), then organizational contact employment and authorization can be approved without verifying this information as described below.
AffirmTrust must be able to confirm all of the following organizational contact requirements:
- Organizational contact’s identity, title, and employment through an independent source.
- Organizational contact is authorized to obtain and approve EV certificates on behalf of the organization. This can be verified through one of the following methods:
- Directly contacting the CEO, COO, or similar executive at the organization and confirming the authority of the organizational contact. If no public records are available regarding the CEO, COO, or other executive, AffirmTrust will attempt to contact the organization’s Human Resources department for contact details.
- A Professional Opinion Letter
Order Verification Requirements
AffirmTrust SSL must verify the certificate request and all certificate details with the organizational contact identified in the certificate request. AffirmTrust SSL must contact the organizational contact using an independently-verified telephone number.
This telephone number is obtained through one of the following methods:
- By researching qualified telephone databases to find a telephone number. Ensure your organization’s primary telephone number is listed in a public telephone directory.
- As provided in a Professional Opinion Letter.
- As confirmed during a site visit conducted by AffirmTrust SSL. During the verification call, AffirmTrust SSL must verify the following with the organizational contact:
- The name of the Certificate Requestor identified in the certificate request and his or her authority to obtain the Extended Validation certificate on behalf of the organization.
- Knowledge of the company’s ownership and right to use the domain identified in the certificate request.
- Approval of the Extended Validation SSL certificate request.
- Acknowledgement of signature of AffirmTrust SSL Certificate Subscriber Agreement that includes all Extended Validation terms and conditions.
Additional Verification requirements
If AffirmTrust SSL is unable to verify any of the required information on your certificate application, we may request that you provide a Professional Opinion Letter from a lawyer or accountant to verify the information.


